IMO Tech Cybersecurity Course Overview

-
Security Control Assessor (SCA)
-
Information System Security Officer
-
ISSO Support Analyst
Future of Cybersecurity Learning
About the Cybersecurity Course with IMO Tech Training
Course Overview
Regulations require that federal agencies undergo a detailed and systematic security assessment process to demonstrate compliance with standards. This is known as the Assessment and Authorization (A&A) formerly called Certification and Accreditation (C&A). Due to increased incidence of cyber-attacks, private organizations are leveraging the Cyber Security standards set forth by the government to protect their assets as well as to be eligible to do business with the government institutions. IMO Tech Training will provide you with the needed training and exposure to prepare you for a role in this growing and demanding IT field. You will be trained for roles such as IT Security Analyst, Security Control Assessor (SCA), Information System Security Officer (ISSO), ISSO Support Analyst, and Vulnerability Assessor.
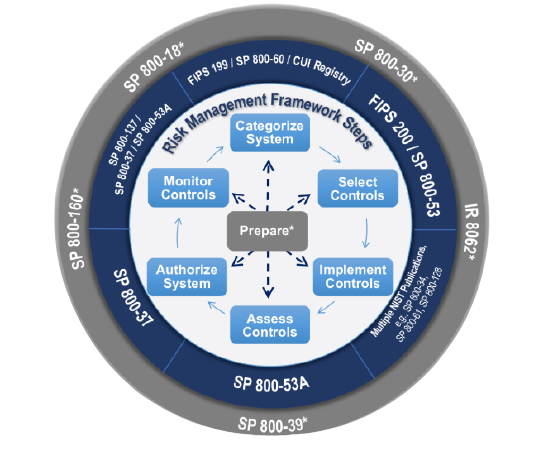
At IMO Tech, our Cyber Security course focuses on Federal Information Security and Modernization Act (FISMA), Assessment and Authorization (A&A) process, the NIST Risk Management Framework (RMF) and an introduction to basic IT network and IT security principles to help you acquire general Cyber Security knowledge. We provide you with IT security compliance skills that are in high demand within the US government and the private sector. To complement the compliance skills, we ensure you understand general Cyber Security technical knowledge to enable you to comprehend and to speak the IT industry language. Our Cyber Security training highlights the following:

Thank you for considering IMO Tech Training as your preferred training provider and hope to see you in class!
